Create Microsoft Entra ID Application based on Authorization Code grant type
The OAuth 2.0 authorization code grant can be used in apps that are installed on a device to gain access to protected resources, such as web APIs. Using the Microsoft identity platform implementation of OAuth 2.0, you can add sign in and API access to your app.
Registering your application establishes a trust relationship between your app and the Microsoft identity platform. The trust is unidirectional: your app trusts the Microsoft identity platform, and not the other way around.
Benefits and Consequences of this Authentication
The use of this type of OAuth 2.0 authentication has various effects on the behavior of COSMO Document Management System.
- Users from Business Central have delegated access to the filing structure in SharePoint Online. This results in an examination of access permissions to the SharePoint Online document libraries. If a user does not have access to a document library, the documents in the DMS Document Box will not be displayed.
- This type of authentication requires Business Central users to log in to SharePoint Online once a day. The login occurs when accessing the first page with the DMS Document Box. The login occurs once per session. Note that an open browser tab corresponds to one session.
Prerequisites
- An Azure account that has an active subscription.
- The Azure account must have permission to manage applications in Microsoft Entra ID (formerly Azure AD). Any of the following Microsoft Entra ID roles include the required permissions:
- Application administrator
- Application developer
- Cloud application administrator
- Completion of the Set up a tenant quickstart.
Register an application
Follow these steps to create the app registration:
Sign in to the Microsoft Azure portal.
Search for and select Microsoft Entra ID.
Under Manage, select App registrations > New registration.
a. Enter a display Name for your application.
b. Specify who can use the application. We recommend using the Accounts in this organizational directory only option.
c. Don't enter anything for Redirect URI (optional). You will configure a redirect URI in the next section.
d. Select Register to complete the initial app registration.
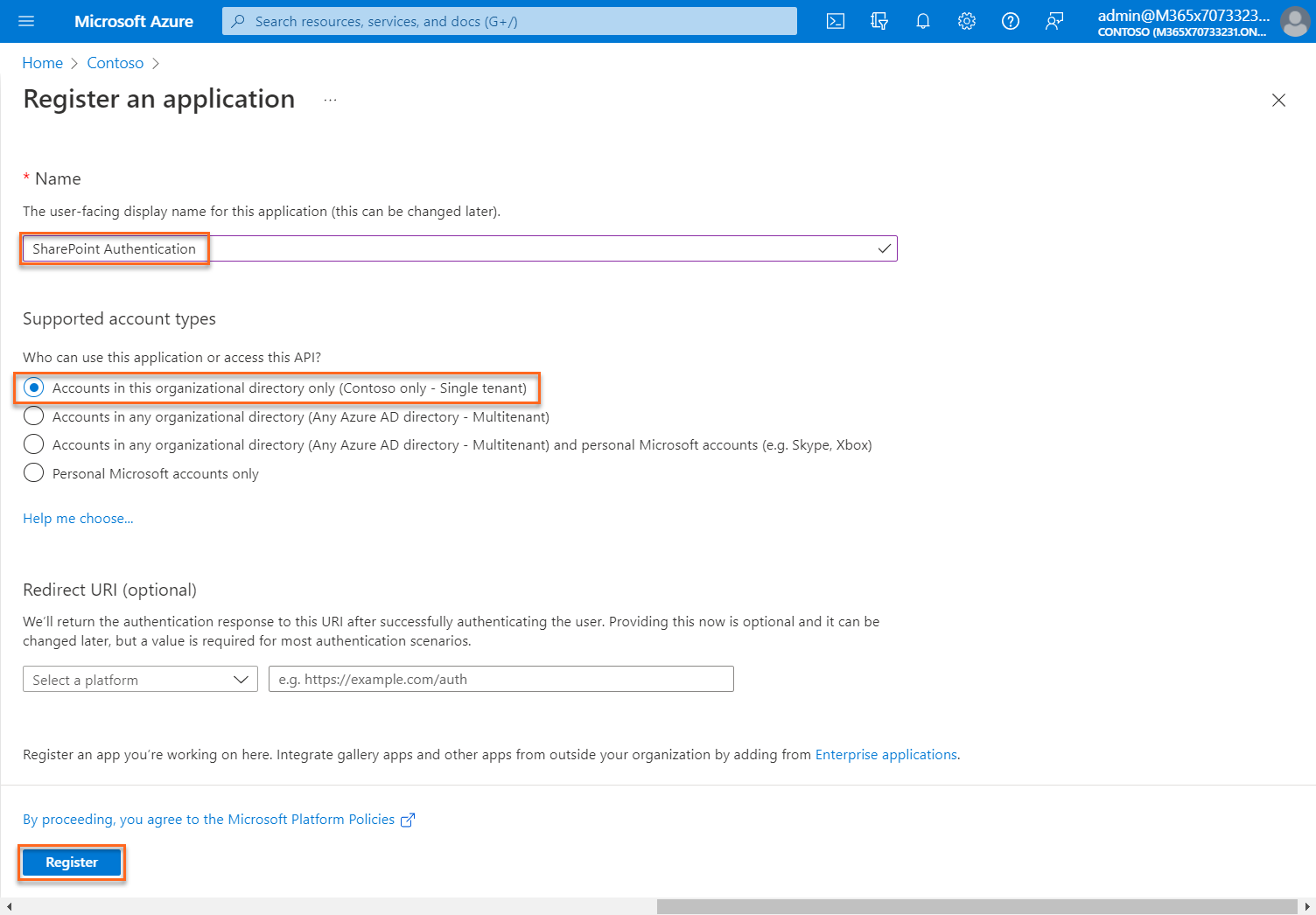
When registration finishes, the Azure portal displays the app registration's Overview pane.
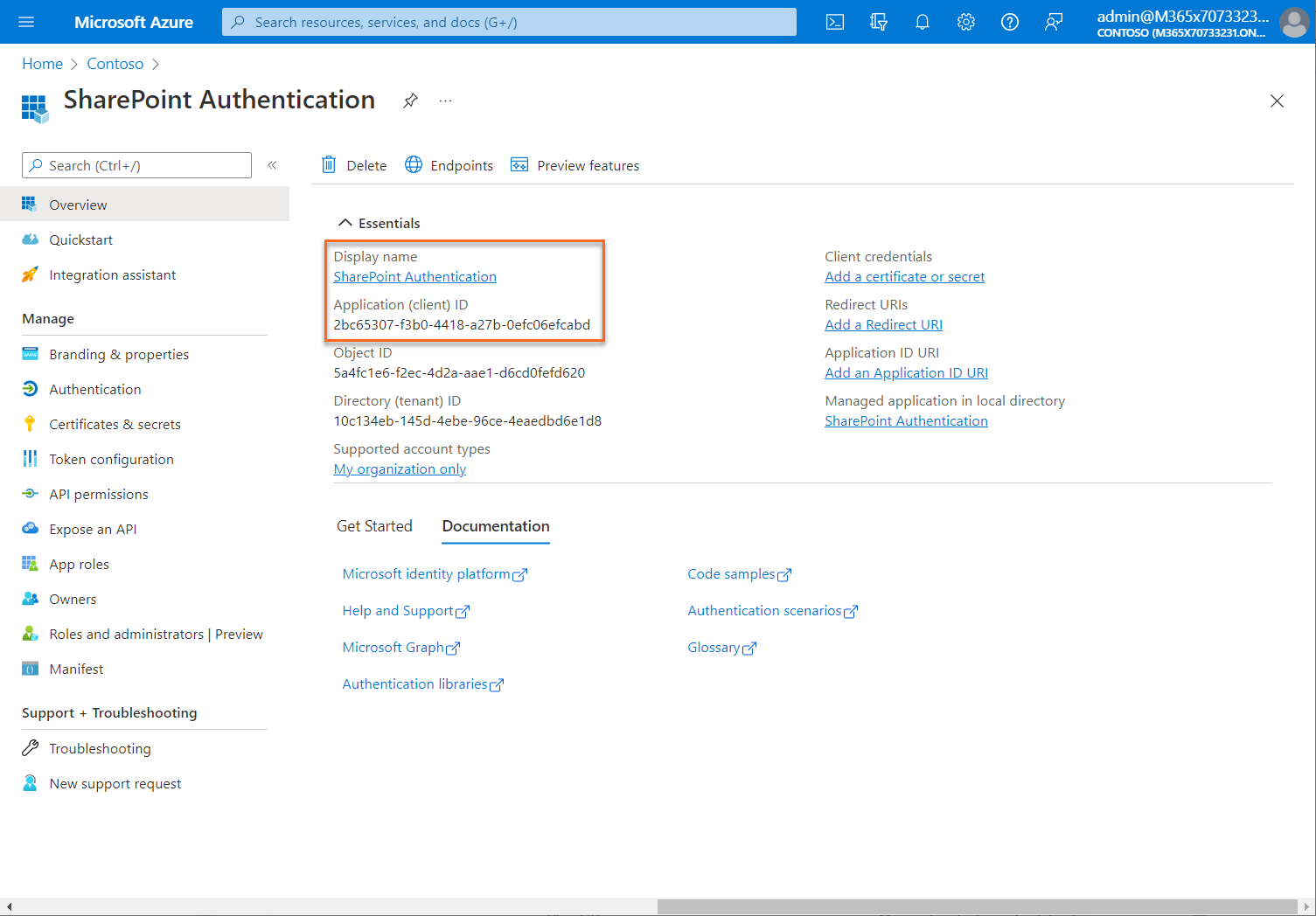
Add a redirect URI
A redirect URI is the location where the Microsoft identity platform redirects a user's client and sends security tokens after authentication. You add and modify redirect URIs for your registered applications by configuring their platform settings.
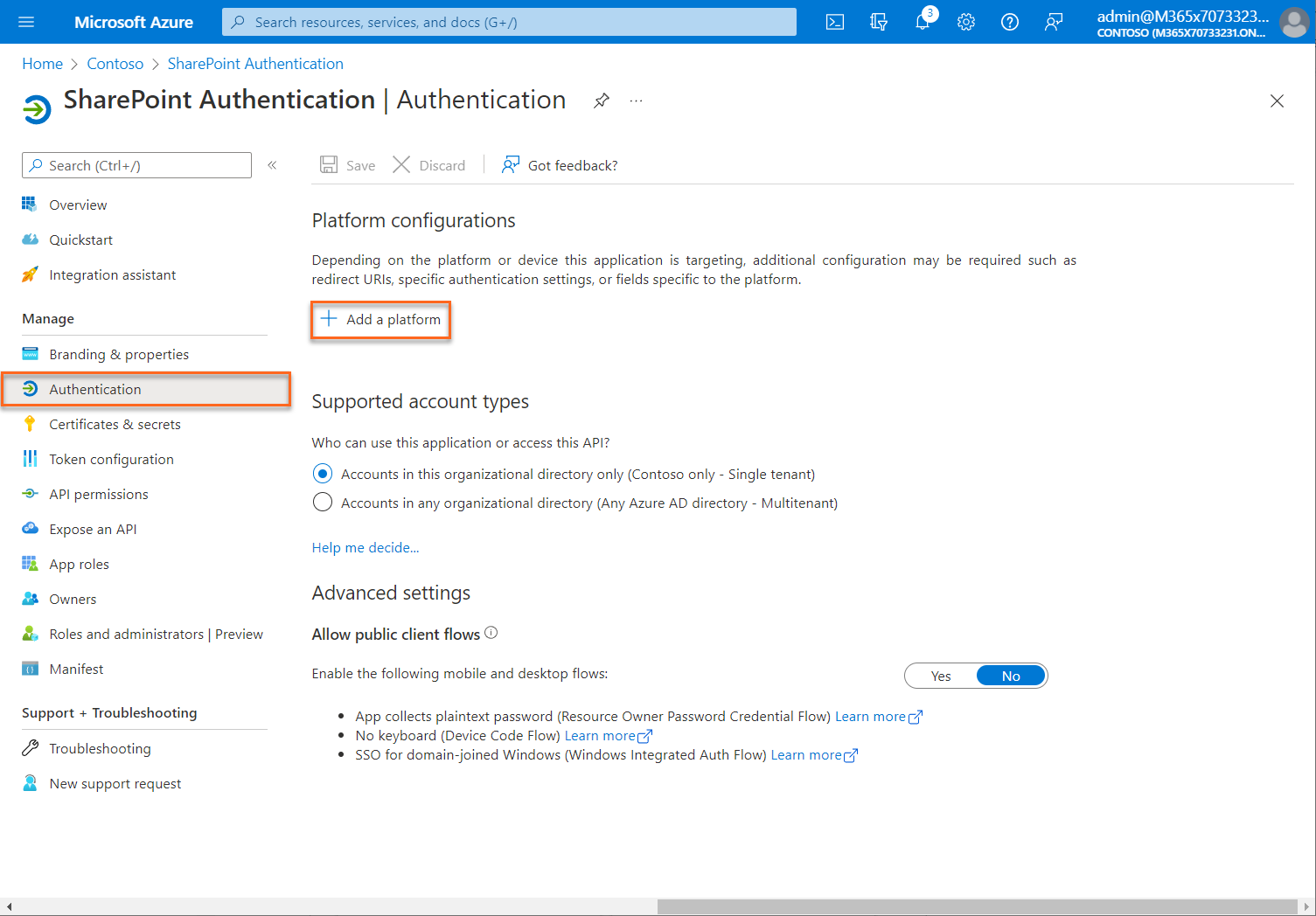
Configure Platform Settings
To configure application settings based on the platform you're targeting, follow these steps:
In the Azure portal, in App registrations, select your application.
Under Manage, select Authentication.
Under Platform configurations, select Add a platform.
Under Configure platforms, select the tile for your application type (platform) to configure its settings.
a. Web - Select this platform for standard web applications that run on a server.
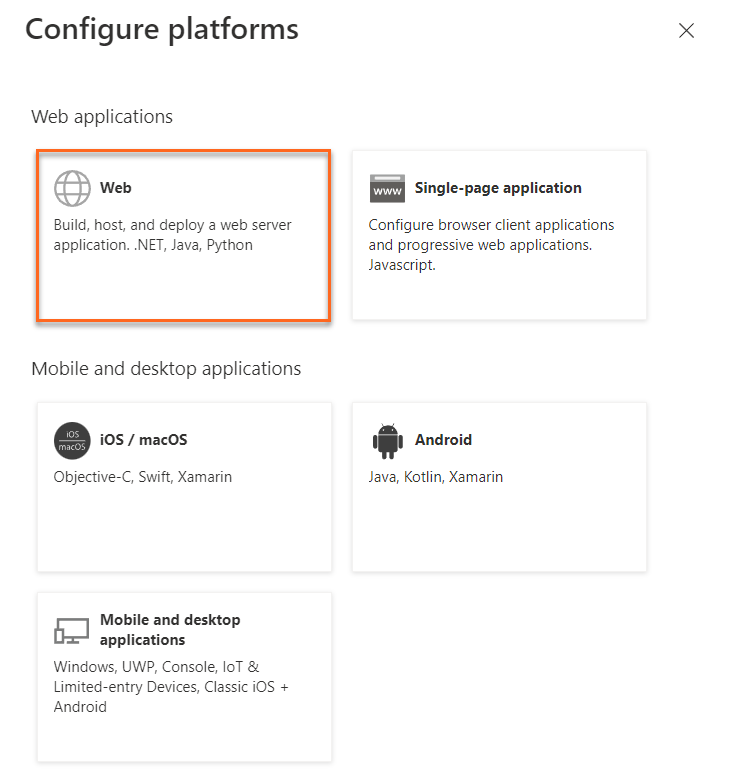
b. Enter a Redirect URI for your app. This URI is the location where the Microsoft identity platform redirects a user's client and sends security tokens after authentication.
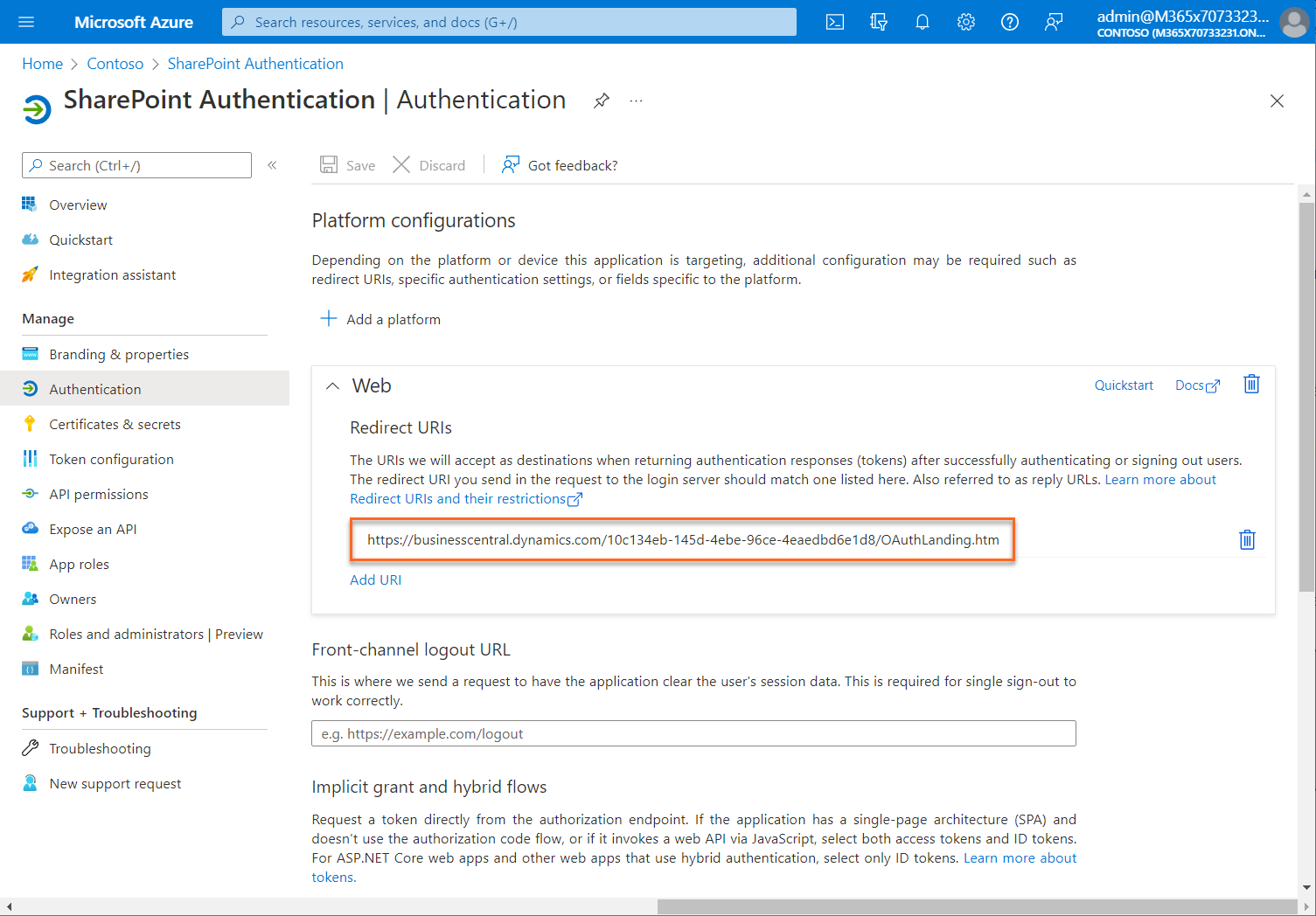
Select Configure to complete the platform configuration.
For restrictions on the format of the redirect URIs, see Redirect URI (reply URL) restrictions and limitations.
Add credentials
Credentials allow your application to authenticate as itself, requiring no interaction from a user at runtime.
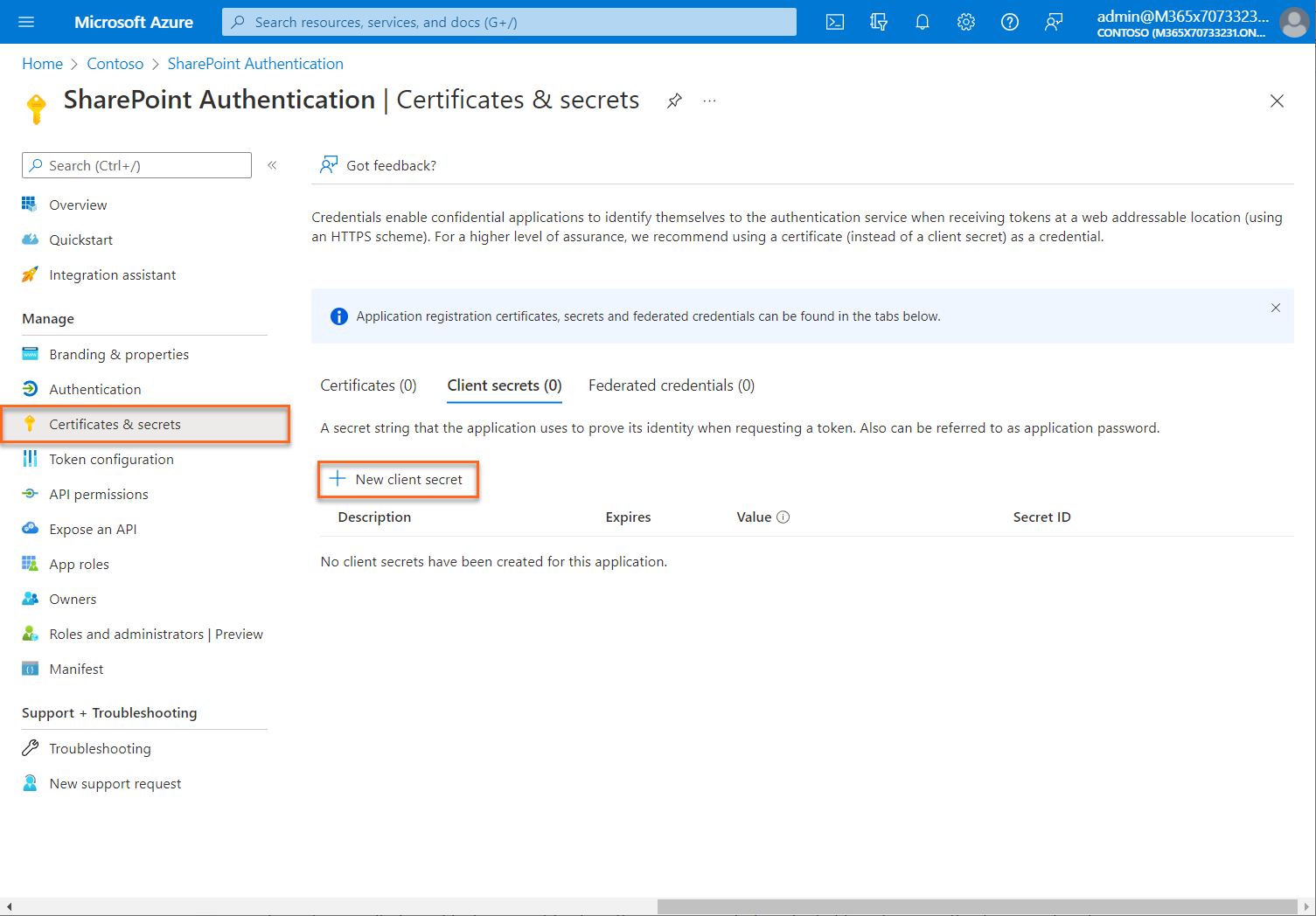
Add a client secret
To add client secrets (a string) as credentials to your confidential client app registration, follow these steps:
In the Azure portal, in App registrations, select your application.
Select Certificates & secrets > Client secrets > New client secret.
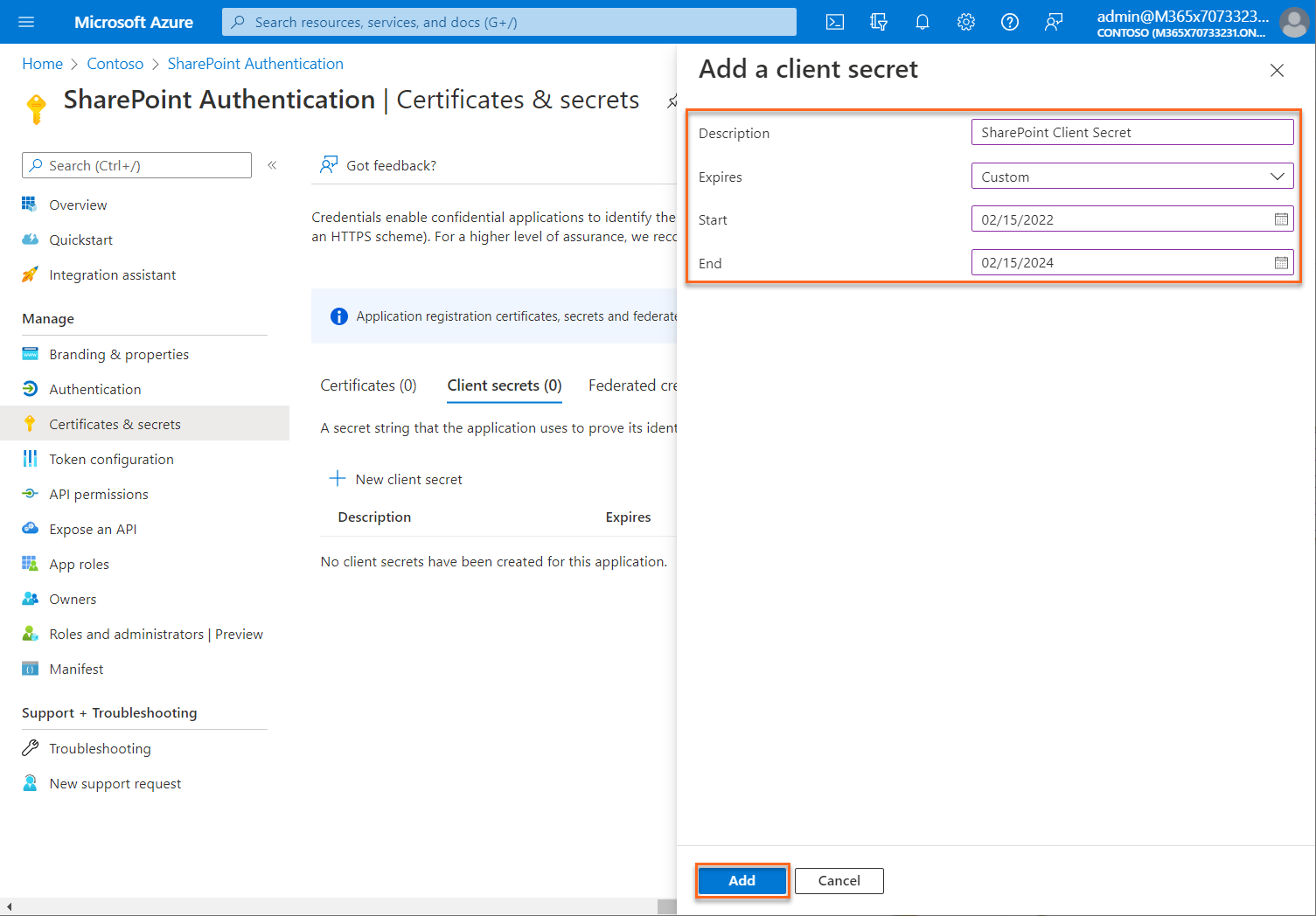
a. Add a description for your client secret.
b. Select an expiration for the secret or specify a custom lifetime. Client secret lifetime is limited to two years (24 months) or less. You can't specify a custom lifetime longer than 24 months.
c. Select Add.
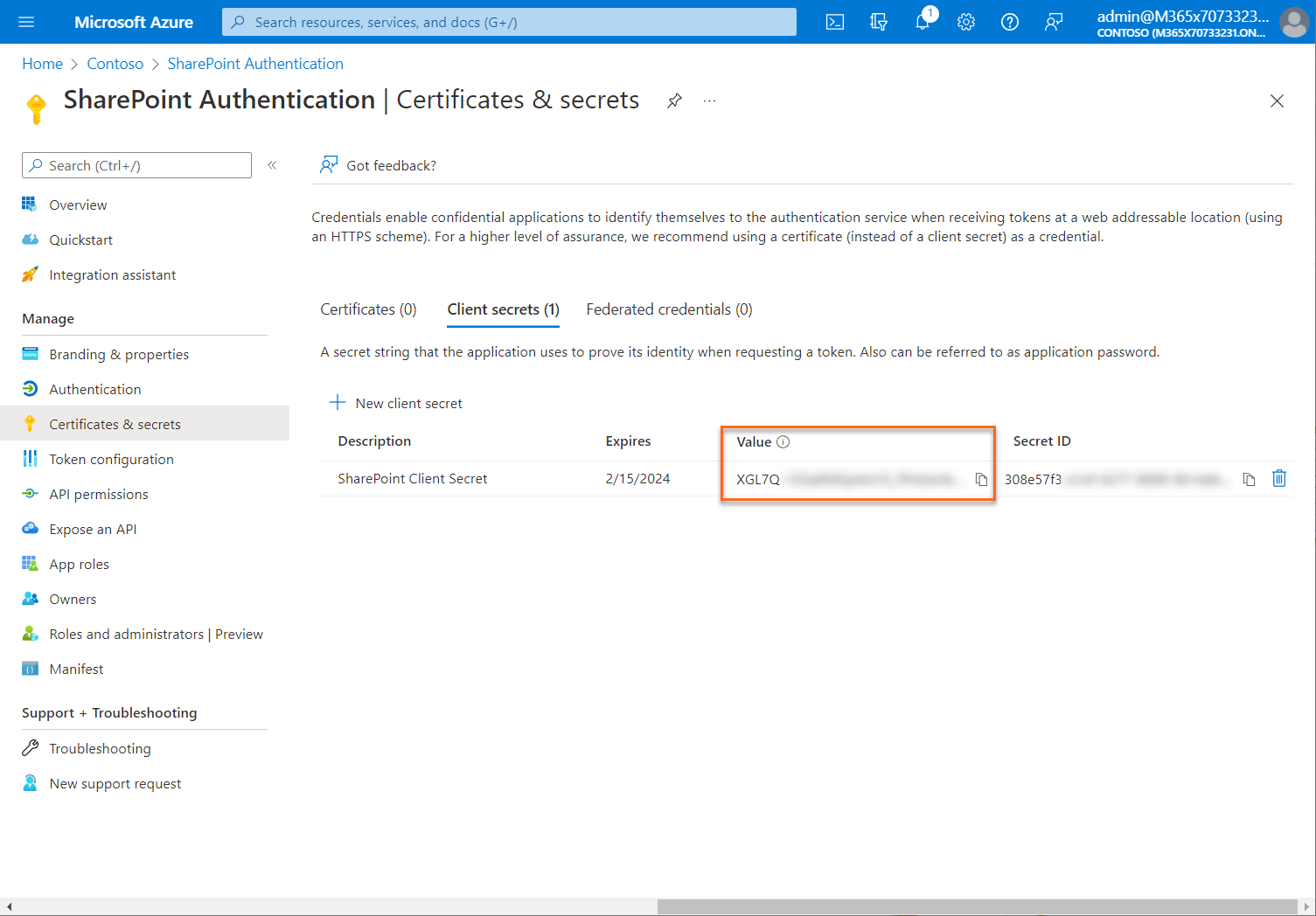
Important
Client secret values cannot be viewed again, except for immediately after creation. Be sure to record the secret's value before you leave the page.
For application security recommendations, see Microsoft identity platform best practices and recommendations.
Add API permissions
Permissions allow your application to perform basic operations.
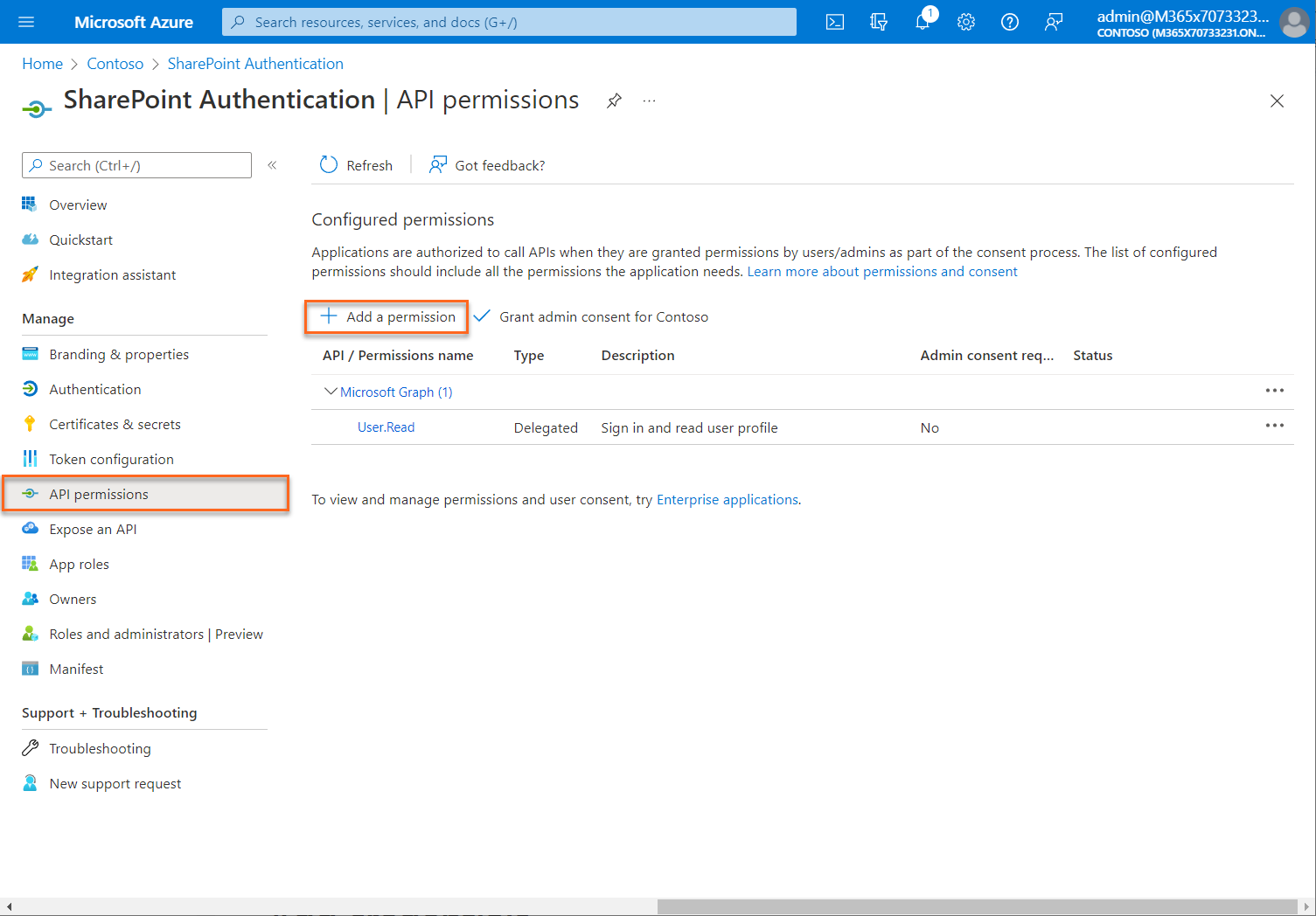
Add permissions to access SharePoint
To configure the client's permissions to the SharePoint API, follow these steps:
In the Azure portal, in App registrations, select your application.
Select API permissions > Add a permission > Microsoft APIs, select SharePoint.
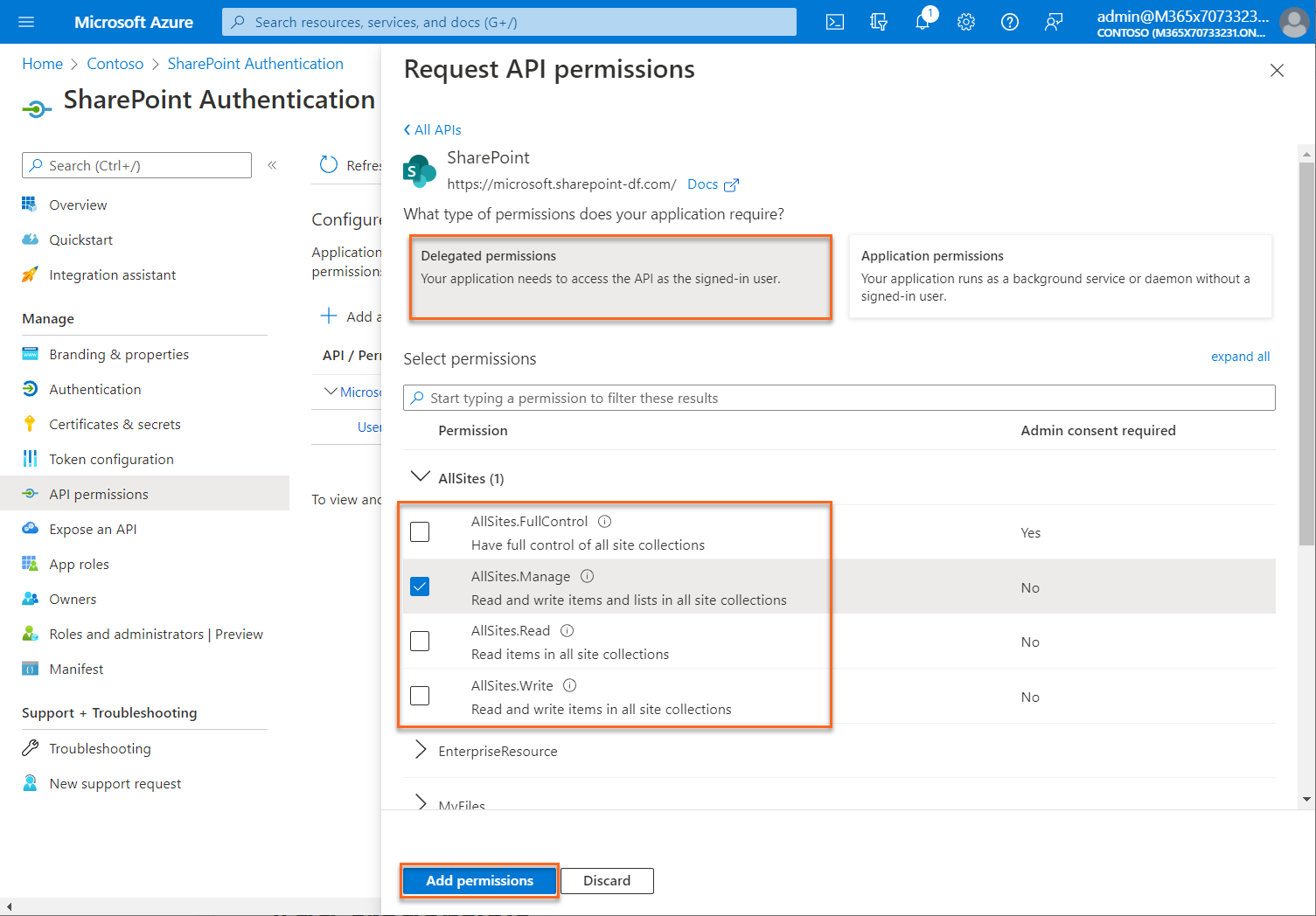
Select the required permission type for the web API.
Delegated permissions is selected by default. Delegated permissions are appropriate for client apps that access a web API as the signed-in user, and whose access should be restricted to the permissions you select in the next step.
Under Select permissions, expand the resource whose scopes you defined for your web API, and select the permissions the client app should have on behalf of the signed-in user.
To execute the library set construction plan, the AllSites.FullControl permission level is required to create web and lists. For reading only, creating, updating, and deleting items in all document libraries and lists in the site collections, the AllSites.Manage permission level is sufficient.
Select Add permissions to complete the process.
The Configured permissions table on the API permissions pane shows the list of permissions that your application requires for basic operation.
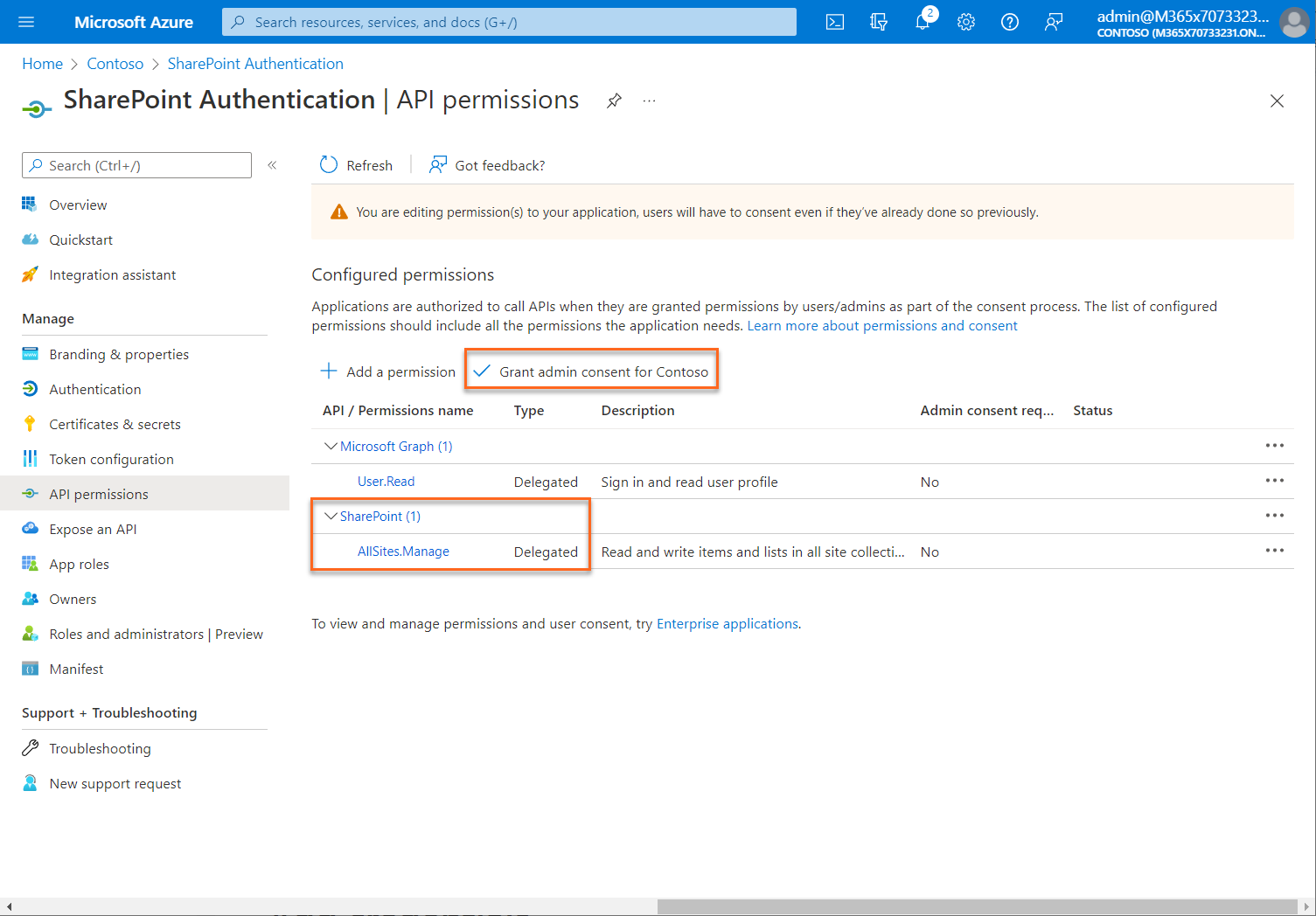
The Grant admin consent for {your tenant} button allows an admin to grant admin consent to the permissions configured for the application. When you select the button, a dialog is shown requesting that you confirm the consent action.
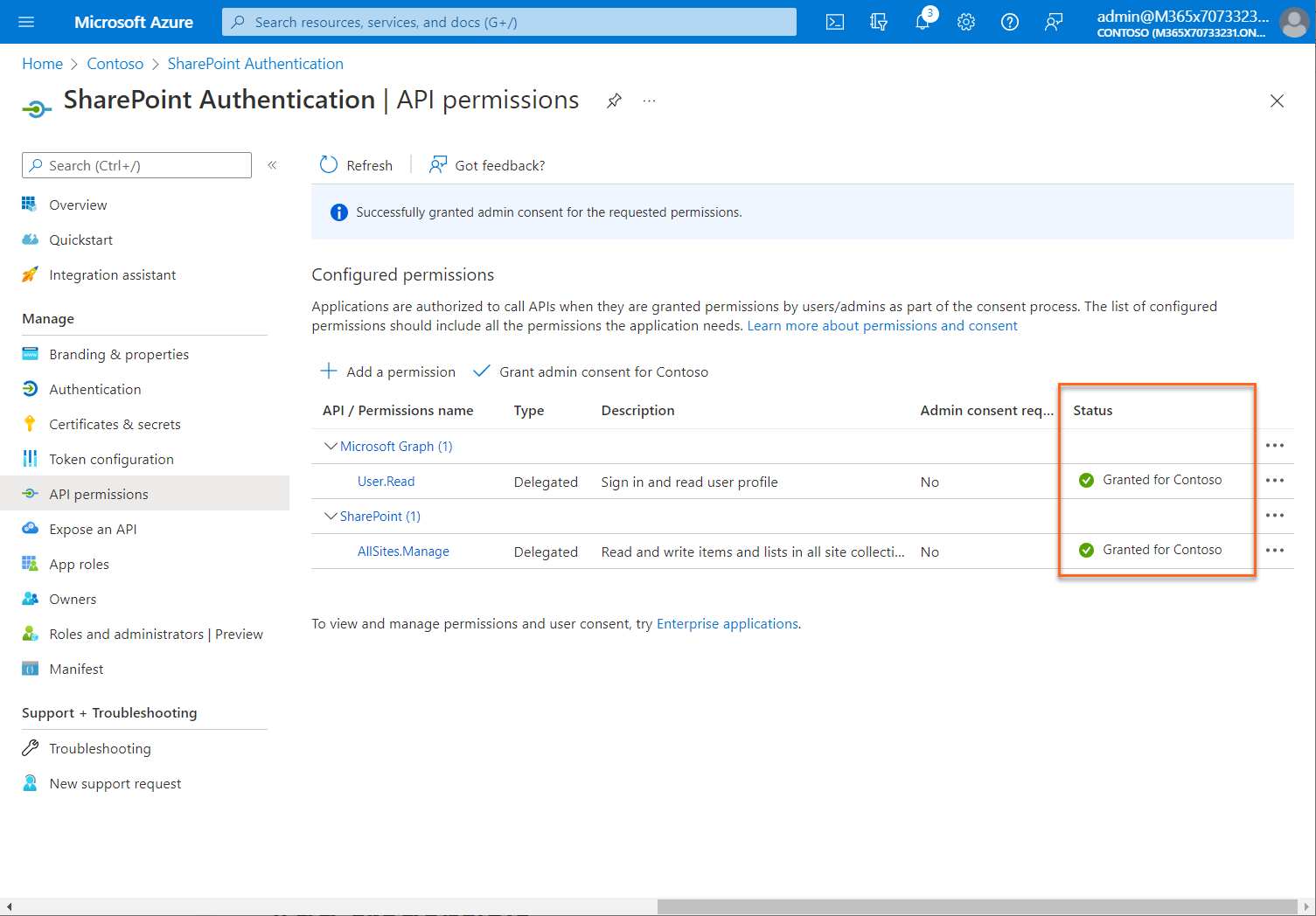
After granting consent, the permissions that required admin consent are shown as having consent granted:
Feedback
Submit feedback for this page.